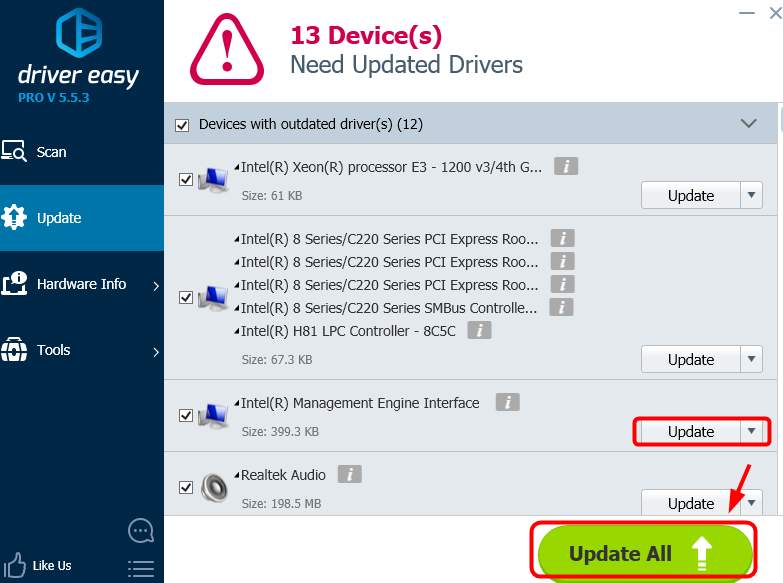
Oct 16, 2015 - The Intel Management Engine Interface (Intel MEI, previously known as. Unofficial windows 7 io seriol controller and touchpad drivers for asus. The Driver Update Tool – is a utility that contains more than 27 million official drivers for all hardware, including intel(r) 7 series/c216 chipset family management engine interface - 1e3a driver. Drivers issue with Intel management Engine Interface and PCI Serial port. Then do the same thing for the PCI simple communications controller (Intel Management Engine Interface device). 0 Kudos Uroš_Roštan. Tutor 11 0 0. Drivers issue with Intel management Engine Interface and PCI Serial port 06:46 AM.
- Intel® Driver & Support Assistant (Intel® DSA) The Intel® Driver & Support Assistant keeps your system up-to-date by providing tailored support and hassle-free updates. Download now Learn more about Intel® DSA before you download ›.
- Solved Do i need Intel Management Engine Driver? System works fine without it. System works fine without it. Solved Intel Management Engine Components Driver Question/Issue.
- Mar 28, 2016 - In Device Manager: Intel Management Engine Interface driver version. Error on a PCI Simple Communications Controller in Device Manager.
- Jun 20, 2018 'Intel(R) Management Engine Interface' hence, the Intel assistant responds with OK, no driver update required. However, two items in 'Device mgr./Other devices' appear with a faulty driver note:-----PCI Serial Port.
By Joseph O., published on June 7, 2016, updated July 12, 2017
Introduction
This document contains information on how to get started with Intel® Active Management Technology (Intel® AMT). It provides an overview of the features, as well as information on minimum system requirements, configuration of an Intel AMT client, and the developer tools available to help create applications for Intel AMT.
Intel AMT supports remote applications running on Microsoft Windows* or Linux*. Intel AMT Release 2.0 and higher supports only Windows-based local applications. For a complete list of system requirements see the Intel AMT Implementation and Reference Guide.
Getting Started
In order to manage an Intel AMT client or run the samples from the SDK, use a separate system to remotely manage your Intel AMT device. Refer to the Intel AMT Implementation and Reference Guide located in the Docs folder of the Intel AMT SDK for more details.
What is Intel® Active Management Technology?
Intel AMT is part of the Intel® vPro™ technology offering. Platforms equipped with Intel AMT can be managed remotely, regardless of its power state or if it has a functioning OS or not.
The Intel® Converged Security and Manageability Engine (Intel® CSME) powers the Intel AMT system. As a component of the Intel® vPro™ platform, Intel AMT uses a number of elements in the Intel vPro platform architecture. Figure 1 shows the relationship between these elements.
Figure 1: Intel® Active Management Technology 11 architecture.
Pay attention to the network connection associated with the Intel® Management Engine (Intel® ME). The NIC changes according to which Intel AMT release you are using.
- The Intel CSME firmware contains the Intel AMT functionality.
- Flash memory stores the firmware image.
- Enable the Intel AMT capability by using Intel CSME as implemented by an OEM platform provider. A remote application performs the enterprise setup and configuration.
- On power-up, the firmware image is copied into the Double Data Rate (DDR) RAM.
- The firmware executes on the Intel® processor with Intel ME and uses a small portion of the DDR RAM (Slot 0) for storage during execution. RAM slot 0 must be populated and powered on for the firmware to run.
Intel AMT stores the following information in flash (Intel ME data):
- OEM-configurable parameters:
- Setup and configuration parameters such as passwords, network configuration, certificates, and access control lists (ACLs)
- Other configuration information, such as lists of alerts and Intel AMT System Defense policies
- The hardware configuration captured by the BIOS at startup
- Details for the 2016 platforms with Intel vPro technology (Release 11.x) are:
- 14nm process
- Platform (mobile and desktop): 6th generation Intel® Core™ processor
- CPU: SkyLake
- PCH: Sunrise Point
What Is new with the Intel® Active Management Technology SDK Release 11.0
- Intel CSME is the new architecture for Intel AMT 11. Prior to Intel AMT 11 Intel CSME was called Intel® Management Engine BIOS Extension (Intel® MEBx).
- MOFs and XSL files: The MOFs and XSL files in the DOCSWS-Management directory and the class reference in the documentation are at version 11.0.0.1139.
- New WS-Eventing and PET table argument fields: Additional arguments added to the CILA alerts provide a reason code for the UI connection and the hostname of the device which generates the alert.
- Updated OpenSSL* version: The OpenSSL version is at v1.0. The redirection library has also been updated.
- Updated Xerces version: Both Windows and Linux have v3.1.2 of the Xerces library.
- HTTPS support for WS events: Secure subscription to WS Events is enabled.
- Remote Secure Erase through Intel AMT boot options: The Intel AMT reboot options has an option to securely erase the primary data storage device.
- DLL signing with strong name: The following DLLs are now signed with a strong name: CIMFramework.dll, CIMFrameworkUntyped.dll, DotNetWSManClient.dll, IWSManClient.dll, and Intel.Wsman.Scripting.dll
- Automatic platform reboot triggered by HECI and Agent Presence watchdogs: An option to automatically trigger a reboot whenever a HECI or Agent Presence watchdog reports that its agent has entered an expired state.
- Replacement of the IDE-R storage redirection protocol: Storage redirection works over the USB-R protocol rather than the IDE-R protocol.
- Updated SHA: The SHA1 certificates are deprecated, with a series of implemented SHA256 certificates.
Configuring an Intel® Active Management Technology Client
Preparing your Intel® Active Management Technology Client for Use
Figure 2 shows the modes, or stages, that an Intel AMT device passes through before it becomes operational.
Figure 2: Configuration flow.
Before configuring an Intel AMT device from the Setup and Configuration Application (SCA), it must be prepared with initial setup information and placed into Setup Mode. The initial information will be different depending on the available options in the Intel AMT release, and the settings performed by the platform OEM. Table 1 summarizes the methods to perform setup and configuration on the different releases of Intel AMT.
| Setup Method | Applicable to Intel® Active Management Technology (Intel® AMT) Releases | For More Information |
|---|---|---|
| Legacy | 1.0; Releases 2.x and 3.x in legacy mode | Setup and Configuration in Legacy Mode |
| SMB | 2.x, 3.x, 4.x, 5.x | Setup and Configuration in SMB Mode |
| PSK | 2.0 Through Intel AMT 10, Deprecated in Intel AMT 11 | Setup and Configuration Using PSK |
| PKI | 2.2, 2.6, 3.0 and later | Setup and Configuration Using PKI (Remote Configuration) |
| Manual | 6.0 and later | Manual Setup and Configuration (from Release 6.0) |
| CCM, ACM | 7.0 and later | Manually Configuring Clients for Intel AMT 7.0 and Later |
Table 1: Setup methods according to Intel® Active Management Technology version.
Intel® Setup and Configuration Software (Intel® SCS) 11 can provision systems back to Intel AMT 2.x. For more information about Intel SCS and provisioning methods as they pertain to the various Intel AMT releases, visit Download the latest version of Intel® Setup and Configuration Service (Intel® SCS)
Manual Configuration Tips
There are no feature limitations when configuring a platform manually since the 6.0 release, but there are some system behaviors to be noted:
- API methods will not return a PT_STATUS_INVALID_MODE status because there is only one mode.
- TLS is disabled by default and must be enabled during configuration. This will always be the case with manual configuration as you cannot set TLS parameters locally.
- The local platform clock will be used until the network time is remotely set. An automatic configuration will not be successful unless the network time was set (and this can only be done after configuring TLS or Kerberos*). Enabling TLS or Kerberos after the configuration will not work if the network time was not set.
- The system enables WEB UI by default.
- The system enables SOL and IDE-R by default.
- The system disables Redirection listener by default starting in Intel AMT 10.
- If KVM is enabled locally via Intel CSME, it still will not be enabled until an administrator activates it remotely.
Starting with Intel AMT 10, some devices are shipped without a physical LAN adapter. These devices cannot be configured using the current USB Key solutions provided by Intel SCS 11.
Manual Setup
During power up, the Intel AMT platform displays the BIOS startup screen, then it processes the MEBx. During this process, access to the Intel MEBX can be made; however the method is BIOS vendor-dependent. Some methods are:
- Most BIOS vendors add entry into Intel CSME via the one-time boot menu. Select the appropriate key (Ctrl+P is typical) and follow the prompts.
- Some OEM platforms prompt you to press <Ctrl+P> after POST. When you press <Ctrl+P>, control passes to the Intel MEBx (Intel CSME) main menu.
- Some OEMs integrate the Intel CSME configuration inside the BIOS (uncommon).
- Some OEMs have an option in the BIOS to show/hide the <Ctrl+P> prompt, so if the prompt is not available in the one-time boot menu check the BIOS to activate the CTRL+P.
Client Control Mode and Admin Control Mode
At setup completion, Intel AMT 7.0 and later devices go into one of two control modes:
- Client Control Mode. Intel AMT enters this mode after performing a basic host-based setup (see Host-Based (Local) Setup). It limits some of Intel AMT functionality, reflecting the lower level of trust required to complete a host-based setup.
- Admin Control Mode. After performing remote configuration, USB configuration, or a manual setup via Intel CSME, Intel AMT enters Admin Control Mode.
There is also a configuration method that performs an Upgrade Client to Admin procedure. This procedure presumes the Intel AMT device is in Client Control Mode, but moves the Intel AMT device to Admin Control mode.
In Admin Control Mode there are no limitations to Intel AMT functionality. This reflects the higher level of trust associated with these setup methods.
Client Control Mode Limitations
When a simple host-based configuration completes, the platform enters Client Control Mode and imposes the following limitations:
- The System Defense feature is not available.
- Redirection (IDE-R and KVM) actions (except initiation of an SOL session) and changes in boot options (including boot to SOL) requires advanced consent. This still allows remote IT support to resolve end-user problems using Intel AMT.
- With a defined Auditor, the Auditor’s permission is not required to perform un-provisioning.
- A number of functions are blocked to prevent an untrusted user from taking control of the platform.
Manually Configuring an Intel Active Management Technology 11.0 Client
The Intel AMT platform displays the BIOS startup screen during power up, then processes the BIOS Extensions. Entry into the Intel AMT BIOS Extension is BIOS vendor-dependent.
If you are using an Intel AMT reference platform (SDS or SDP), the display screen prompts you to press <Ctrl+P>. Then the control passes to the Intel CSME main menu.
In the case of it being a OEM system It is still easy to use the one-time boot menu, although entry into Intel CSME is usually an included option as part of the one-time boot menu. The exact key sequence varies by OEM, BIOS and Model.
Manual Configuration for Intel® AMT 11.0 Clients with Wi-Fi*-Only Connection
Many systems no longer have a wired LAN connector. You can configure and activate the Intel ME, then via WebUI or some alternate method to push the wireless settings.
- Change the default password to a new value (required to proceed). The new value must be a strong password. It should contain at least one uppercase letter, one lowercase letter, one digit, and one special character, and be at least eight characters.
- Enter Intel CSME during startup.
- Enter the Default Password of “admin”.
- Enter and confirm New Password.
- Select Intel AMT Configuration.
- Select/Verify Manageability Feature Selection is Enabled.
- Select Activate Network Access.
- Select “Y” to confirm Activating the interface.
- Select Network Setup.
- Select Intel® ME network Name Settings.
- Enter Host Name.
- Enter Domain Name.
- Select User Consent.
- By default, this is set for KVM only; can be changed to none or all.
- Exit Intel CSME.
- Configure Wireless via ProSet Wireless Driver synching, WebUI, or an alternative method.
Manual Configuration for Intel AMT 11.0 Clients with LAN Connection
Enter the Intel CSME default password (“admin”).
Change the default password (required to proceed). The new value must be a strong password. It should contain at least one uppercase letter, one lowercase letter, one digit, and one special character, and be at least eight characters. A management console application can change the Intel AMT password without modifying the Intel CSME password.
- Select Intel AMT Configuration.
- Select/Verify Manageability Feature Selection is Enabled.
- Select Activate Network Access.
- Select “Y” to confirm Activating the interface.
- Select Network Setup.
- Select Intel ME network Name Settings.
- Enter Host Name.
- Enter Domain Name.
- Select User Consent.
- By default, this is set for KVM only; can be changed to none or all.
- Exit Intel CSME.
Accessing Intel® Active Management Technology via the WebUI Interface
An administrator with user rights can remotely connect to the Intel AMT device via the Web UI by entering the URL of the device. Depending on whether TLS has been activated, the URL will change:
- Non-TLS - http:// <IP_or_FQDN>:16992
- TLS - https:// <FQDN_only>:16993
You can also use a local connection using the host’s browser for a non TLS connection. Use either localhost or 127.0.0.1 as the IP address. Example: http://127.0.0.1:16992
Intel Active Management Technology Support Requirements
In addition to having the BIOS and Intel CSME configured correctly, the Wireless NIC needs to be Intel AMT Compliant. Specific drivers and services must be present and running in order to use the Intel AMT to manage the host OS.
To verify that the Intel AMT drivers and services are loaded correctly, look for them in the Device Manger and Services in the host OS. Frequently check the OEM’s download site for upgraded versions of the BIOS, firmware, and drivers.
Here are the drivers and services that should appear in the host OS:
- Intel® Ethernet Network Connection i218-LM #
- Intel® Dual Band Wireless-AC 8260 or similar #
- Intel® Management Engine Interface (Intel® MEI) driver
- Serial-Over-LAN (SOL) driver
- Intel® Management and Security Status (Intel® MSS) Application Local Management Service**
- Intel® AMT Management and Security Status application**
- HID mouse and keyboard drivers***
* Network controller and wireless interface versions will vary depending on the generation of the Intel vPro platform.
** Part of the complete Intel MEI (Chipset) Driver package How to remove free download manager.
*** HID Drivers are needed when connecting via Intel AMT KVM. These default drivers are not normally an issue; however, we have seen issues on stripped-down custom OS installs. If a connection is made to a device without the HID drivers, the OS tries to auto-download the drivers. Once the install is done, reconnect the KVM connection.
Note: The version level of the drivers must match the version level of the firmware and BIOS. If non-compatible versions are installed, Intel AMT will not work with the features that require those interfaces.
Physical Device - Wireless Ethernet Connection
By default, any wireless Intel vPro platform will have an Intel AMT enabled wireless card installed, such as an Intel Dual Band Wireless-AC 8260. Any wireless card other than one from Intel will not have wireless Intel AMT capabilities. If you have a card other than the Intel Dual Band Wireless-AC 8260 you can use ark.intel.com to verify whether the wireless card is Intel AMT compliant.
Windows OS Required Software
Device drivers are not necessary for remote management; however, they are essential for local communication to the firmware. Functions like discovery or configuration via the OS will require the Intel MEI driver, SOL driver, LMS service and Intel® Management and Security Status (Intel® MSS).
Device Drivers - Intel® Management Engine Interface
Intel MEI is required to communicate to the firmware. The Windows automatic update installs the Intel MEI driver by default. The Intel MEI driver should stay in version step with the Intel MEBX version.
The Intel MEI driver is in the Device Manager under “System devices” as “Intel® Management Engine Interface.”
Device Drivers - Serial-Over-LAN Driver
The SOL driver used during redirection operation where a remote CD drive is mounted during a IDE redirection operation.
The SOL driver is in the Device Manager under “Ports” as “Intel® Active Management Technology – SOL (COM3).”
Figure 3: Serial-Over-LAN driver.
Service - Intel Active Management Technology LMS Service
The Local Manageability Service (LMS) runs locally in an Intel AMT device and enables local management applications to send requests and receive responses. The LMS responds to the requests directed at the Intel AMT local host and routes them to the Intel® ME via the Intel® MEI driver. This service installer is packaged with the Intel MEI drivers on the OEM websites.
Please note that when installing the Windows OS, the Windows Automatic Update service installs the Intel MEI driver only. IMSS and the LMS Service are not installed. The LMS service communicates from an OS application to the Intel MEI driver. If the LMS service is not installed, go to the OEM website and download the Intel MEI driver, which is usually under the Chipset Driver category.
Figure 4: Intel® Management Engine Interface driver.
The LMS is a Windows service installed on the host platform that has Intel AMT Release 9.0 or greater. Prior to this, the LMS was known as the User Notification Service (UNS) starting from Intel AMT Release 2.5 to 8.1.
The LMS receives a set of alerts from the Intel AMT device. LMS logs the alert in the Windows Application event log. To view the alerts, right-click My Computer, and then select Manage>System Tools>Event Viewer>Application.
Tool - Intel® Management and Security Status Tool
The Intel MSS tool can be accessed by the blue-key icon in the Windows tray.
Figure 5: Sys Tray Intel® Management and Security Status icon.
General tab
The General tab of the Intel MSS tool shows the status of Intel vPro features available on the platform and an event history. Each tab has additional details.
Figure 6: Intel® Management and Security Status General tab.
Intel AMT Tab
This interface allows the local user to terminate KVM and Media Redirection operations, perform a Fast Call for Help, and see the System Defense state.
Figure 7: Intel® Management and Security Status Intel AMT tab.
Advanced Tab
The Advanced tab of the Intel MSS tool shows more detailed information on the configuration of Intel AMT and its features. The screenshot in Figure 8 verifies that Intel AMT has been configured on this system.
Figure 8:Intel® Management and Security Status Advanced tab.
Intel Active Management Technology Software Development Kit (SDK)
Android project download. TheIntel AMT Software Development Kit (SDK) provides low-level programming capabilities so developers can build manageability applications that take full advantage of Intel AMT.
The Intel AMT SDK provides sample code and a set of APIs that let developers easily and quickly incorporate Intel AMT support into their applications. The SDK also includes a full set of HTML documentation.
The SDK supports C++ and C# on Microsoft Windows and Linux operating systems. Refer to the user guide and the Readme files in each directory for important information on building the samples.
The SDK, as delivered, is a set of directories that can be copied to any location. The directory structure should be copied in its entirety due to the interdependencies between components. There are three folders at the top level: DOCS (contains SDK documentation), and one each for Linux and Windows (sample code.) For more information on how to get started and how to use the SDK, see the Intel® AMT Implementation and Reference Guide.
As illustrated by the screenshot in Figure 9 of the Intel® AMT Implementation and Reference Guide, you can get more information on system requirements and how to build the sample code by reading the Using the Intel® AMT SDK section. The documentation is available on the Intel® Software Network here: Intel® AMT SDK (Latest Release)
Figure 9: Intel AMT Implementation and Reference Guide
Other Intel Active Management Technology Resources
Intel AMT Implementation and Reference Guide
Intel AMT SDK Download
High-level API Article and download
Intel® Platform Solutions Manager Article and Download
Power Shell Module download
KVM Application Developer’s Guide
Redirection Library
C++ CIM Framework API
C# CIM Framework API
Intel® ME WMI Provider
System Health Validation (NAP)
Use Case Reference Designs
Intel Management Engine Driver
Appendix
The following table provides a snapshot of features supported by Intel AMT Releases 8 through 11.
/psp-angry-birds-iso-download.html. Read about all the features in the Intel AMT SDK Implementation and Reference Guide (“Intel AMT Features” section.)
| Feature | Intel® Active Management Technology (Intel® AMT) 8 | Intel AMT 9 | Intel AMT 10 | Intel AMT 11 |
|---|---|---|---|---|
| Hardware Inventory | X | X | X | X |
| Persistent ID | X | X | X | X |
| Remote Power On/Off | X | X | X | X |
| SOL/IDER | X | X | X | X |
| Event Management | X | X | X | X |
| Third-Party Data Storage | X | X | X | X |
| Built-in Web Server | X | X | X | X |
| Flash Protection | X | X | X | X |
| Firmware Update | X | X | X | X |
| HTTP Digest/ TLS | X | X | X | X |
| Static and Dynamic IP | X | X | X | X |
| System Defense | X | X | X | X |
| Agent Presence | X | X | X | X |
| Power Policies | X | X | X | X |
| Feature | AMT 8 | AMT 9 | AMT 10 | AMT 11 |
| Mutual Authentication | X | X | X | X |
| Kerberos* | X | X | X | X |
| TLS-PSK | X | X | X | Deprecated |
| Privacy Icon | X | X | X | X |
| Intel® Management Engine Wake-on-LAN | X | X | X | X |
| Remote Configuration | X | X | X | X |
| Wireless Configuration | X | X | X | X |
| Endpoint Access Control (EAC) 802.1 | X | X | X | X |
| Power Packages | X | X | X | X |
| Environment Detection | X | X | X | X |
| Event Log Reader Realm | X | X | X | X |
| System Defense Heuristics | X | X | X | X |
| WS-MAN Interface | X | X | X | X |
| Network Interfaces | X | X | X | X |
| Feature | AMT 8 | AMT 9 | AMT 10 | AMT 11 |
| Fast Call For Help (CIRA) | X | X | X | X |
| Access Monitor | X | X | X | X |
| Microsoft NAP* Support | X | X | X | X |
| Virtualization Support for Agent Presence | X | X | X | X |
| PC Alarm Clock | X | X | X | X |
| KVM Remote Control | X | X | X | X |
| Wireless Profile Synchronization | X | X | X | X |
| Support for Internet Protocol Version 6 | X | X | X | X |
| Host-Based Provisioning | X | X | X | X |
| Graceful Shutdown | X | X | X | X |
| WS-Management API | X | X | X | X |
| SOAP Commands | X | Deprecated | Deprecated | Deprecated |
| InstantGo Support | X | |||
| Remote Secure Erase | X |
Intel Management Engine Controller Driver Windows 10
The Intel Management Engine (ME), also known as the Manageability Engine,[1][2] is an autonomous subsystem that has been incorporated in virtually all of Intel's processorchipsets since 2008.[3][4][1] It is located in the Platform Controller Hub of modern Intel motherboards. It is a part of Intel Active Management Technology, which allows system administrators to perform tasks on the machine remotely[5]. System administrators can use it to turn the computer on and off, and they can login remotely into the computer regardless of whether or not an operating system is installed.[6]
The Intel Management Engine always runs as long as the motherboard is receiving power, even when the computer is turned off.
The IME is an attractive target for hackers, since it has top level access to all devices and completely bypasses the operating system. Intel has not released much information on the Intel Management Engine, prompting speculation that it may include a backdoor. The Electronic Frontier Foundation has voiced concern about IME.
AMD processors have a similar feature, called AMD Secure Technology.
- 1Design
- 1.2Firmware
- 2Security vulnerabilities
- 2.1Disabling the ME
- 2.1.1Undocumented methods
- 2.6SA-00086
- 2.1Disabling the ME
- 4Reactions
Design[edit]
The subsystem primarily consists of proprietary firmware running on a separate microprocessor that performs tasks during boot-up, while the computer is running, and while it is asleep.[7] As long as the chipset or SoC is connected to current (via battery or power supply), it continues to run even when the system is turned off.[8] Intel claims the ME is required to provide full performance.[9] Its exact workings[10] are largely undocumented[11] and its code is obfuscated using confidential huffman tables stored directly in hardware, so the firmware does not contain the information necessary to decode its contents.[12] Intel's main competitor AMD has incorporated the equivalent AMD Secure Technology (formally called Platform Security Processor) in virtually all of its post-2013 CPUs.[13]
Hardware[edit]
Starting with ME 11, it is based on the Intel Quark x86-based 32-bit CPU and runs the MINIX 3 operating system.[14] The ME state is stored in a partition of the SPI flash, using the Embedded Flash File System (EFFS).[15] Previous versions were based on an ARC core, with the Management Engine running the ThreadXRTOS. Versions 1.x to 5.x of the ME used the ARCTangent-A4 (32-bit only instructions) whereas versions 6.x to 8.x used the newer ARCompact (mixed 32- and 16-bitinstruction set architecture). Starting with ME 7.1, the ARC processor could also execute signed Java applets.
The ME has its own MAC and IP address for the out-of-band interface, with direct access to the Ethernet controller; one portion of the Ethernet traffic is diverted to the ME even before reaching the host's operating system, for what support exists in various Ethernet controllers, exported and made configurable via Management Component Transport Protocol (MCTP).[16][17] The ME also communicates with the host via PCI interface.[15] Under Linux, communication between the host and the ME is done via /dev/mei.[18]
Until the release of Nehalem processors, the ME was usually embedded into the motherboard's northbridge, following the Memory Controller Hub (MCH) layout.[19] With the newer Intel architectures (Intel 5 Series onwards), ME is included into the Platform Controller Hub (PCH).[20][21]
Firmware[edit]
By Intel's current terminology as of 2017, ME is one of several firmware sets for the Converged Security and Manageability Engine (CSME). Prior to AMT version 11, CSME was called Intel Management Engine BIOS Extension (Intel MEBx).[1]
- Management Engine (ME) – mainstream chipsets[22]
- Server Platform Services (SPS) – server chipsets and SoCs[23][22][24]
- Trusted Execution Engine (TXE) – tablet/embedded/low power[25][26]
The Russian company Positive Technologies (Dmitry Sklyarov) found that the ME firmware version 11 runs MINIX 3.[27][28][29]
Modules[edit]
- Active Management Technology (AMT)[2]
- Alert Standard Format (ASF) support[citation needed]
- Intel Boot Guard (IBG)[30] and Secure Boot[26]
- Integrated Clock Controller (ICC)[citation needed]
- Quiet System Technology (QST), formerly known as Advanced Fan Speed Control (AFSC), which provides support for acoustically-optimized fan speed control, and monitoring of temperature, voltage, current and fan speed sensors that are provided in the chipset, CPU and other devices present on the motherboard. Communication with the QST firmware subsystem is documented and available through the official software development kit (SDK).[31]
- Protected Audio Video Path (used in PlayReady DRM)[citation needed]
- Intel Security Assist (ISA)[citation needed]
- Serial over LAN (SOL)[32]
- Firmware-based Trusted Platform Module (TPM)[30]
Security vulnerabilities[edit]
Several weaknesses have been found in the ME. On May 1, 2017, Intel confirmed a Remote Elevation of Privilege bug (SA-00075) in its Management Technology.[33] Every Intel platform with provisioned Intel Standard Manageability, Active Management Technology, or Small Business Technology, from Nehalem in 2008 to Kaby Lake in 2017 has a remotely exploitable security hole in the ME.[34][35] Several ways to disable the ME without authorization that could allow ME's functions to be sabotaged have been found.[36][37][38] Additional major security flaws in the ME affecting a very large number of computers incorporating ME, Trusted Execution Engine (TXE), and Server Platform Services (SPS) firmware, from Skylake in 2015 to Coffee Lake in 2017, were confirmed by Intel on 20 November 2017 (SA-00086).[39] Unlike SA-00075, this bug is even present if AMT is absent, not provisioned or if the ME was 'disabled' by any of the known unofficial methods.[40] In July 2018 another set of vulnerabilitites were disclosed (SA-00112).[41] In September 2018, yet another vulnerability was published (SA-00125).[42]
Disabling the ME[edit]
It is normally not possible for the user to disable the ME. Potentially risky, undocumented methods to do so were discovered, however.[39] These methods are not supported by Intel. The ME's security architecture is supposed to prevent disabling, and thus its possibility is considered a security vulnerability. For example, a virus could abuse it to make the computer lose some of the functionality that the typical end-user expects, such as the ability to play media with DRM. Yet, critics consider the weaknesses not as bugs, but as features.
Strictly speaking, none of the known methods disables the ME completely, since it is required for booting the main CPU. All known methods merely make the ME go into abnormal states soon after boot, in which it seems not to have any working functionality. The ME is still physically connected to the current and its microprocessor is continuing to execute code.
Undocumented methods[edit]
Firmware neutering[edit]
In 2016, the me_cleaner project found that the ME's integrity verification is broken. The ME is supposed to detect that it has been tampered with, and, if this is the case, shut down the PC forcibly after 30 minutes.[43] This prevents a compromised system from running undetected, yet allows the owner to fix the issue by flashing a valid version of the ME firmware during the grace period. As the project found out, by making unauthorized changes to the ME firmware, it was possible to force it into an abnormal error state that prevented triggering the shutdown even if large parts of the firmware had been overwritten and thus made inoperable.
'High Assurance Platform' mode[edit]
In August 2017, Russian company Positive Technologies (Dmitry Sklyarov) published a method to disable the ME via an undocumented built-in mode. As Intel has confirmed[44] the ME contains a switch to enable government authorities such as the NSA to make the ME go into High-Assurance Platform (HAP) mode after boot. This mode disables most of ME's functions.[45][46] It is authorized for use by government authorities only and is supposed to be available only in machines produced for them. Yet it turned out that most machines sold on the retail market can be tricked into activating the switch.[47][48]. Manipulation of the HAP bit was quickly incorporated into the me_cleaner project[49].
Commercial ME disablement[edit]
In late 2017, several laptop vendors announced their intentions to ship laptops with the Intel ME disabled:
- Purism previously petitioned Intel to sell processors without the ME, or release its source code, calling it 'a threat to users' digital rights'.[50] In March 2017, Purism announced[51] that it had neutralized the ME by erasing the majority of the ME code from the flash memory. It further announced in October 2017[52] that new batches of their Debian-based Librem line of laptops will ship with the ME neutralized (via erasing the majority of ME code from the flash, as previously announced), and additionally disabling most ME operation via the HAP bit. Updates for existing Librem laptops were also announced.
- System 76 announced in November 2017[53] their plan to disable the ME on their new and recent Ubuntu-based machines via the HAP bit.
- Dell, in December 2017,[54] began showing certain laptops on its website that offered the 'Systems Management' option 'Intel vPro - ME Inoperable, Custom Order' for an additional fee. Dell has not announced or publicly explained the methods used. In response to press requests, Dell stated that those systems had been offered for quite a while, but not for the general public, and had found their way to the website only inadvertently.[55] The laptops are available only by custom order and only to military, government and intelligence agencies.[56] They are specifically designed for covert operations, such as providing a very robust case and a 'stealth' operating mode kill switch that disables display, LED lights, speaker, fan and any wireless technology.[57]
Effectiveness against vulnerabilities[edit]
None of the two methods to disable the ME discovered so far turned out to be an effective countermeasure against the SA-00086 vulnerability.[58] This is because the vulnerability is in an early-loaded ME module that is essential to boot the main CPU.[59]
Ring −3 rootkit[edit]
A ring −3 rootkit was demonstrated by Invisible Things Lab for the Q35 chipset; it does not work for the later Q45 chipset as Intel implemented additional protections.[60] The exploit worked by remapping the normally protected memory region (top 16 MB of RAM) reserved for the ME. The ME rootkit could be installed regardless of whether the AMT is present or enabled on the system, as the chipset always contains the ARC ME coprocessor. (The '−3' designation was chosen because the ME coprocessor works even when the system is in the S3 state, thus it was considered a layer below the System Management Mode rootkits.[19]) For the vulnerable Q35 chipset, a keystroke logger ME-based rootkit was demonstrated by Patrick Stewin.[61][62]
Zero-touch provisioning[edit]
Another security evaluation by Vassilios Ververis showed serious weaknesses in the GM45 chipset implementation. In particular, it criticized AMT for transmitting unencrypted passwords in the SMB provisioning mode when the IDE redirection and Serial over LAN features are used. It also found that the 'zero touch' provisioning mode (ZTC) is still enabled even when the AMT appears to be disabled in BIOS. For about 60 euros, Ververis purchased from Go Daddy a certificate that is accepted by the ME firmware and allows remote 'zero touch' provisioning of (possibly unsuspecting) machines, which broadcast their HELLO packets to would-be configuration servers.[63]
SA-00075 (aka Silent Bob is Silent)[edit]
In May 2017, Intel confirmed that many computers with AMT have had an unpatched critical privilege escalation vulnerability (CVE-2017-5689).[35][64][33][65][66] The vulnerability, which was nicknamed 'Silent Bob is Silent' by the researchers who had reported it to Intel,[67] affects numerous laptops, desktops and servers sold by Dell, Fujitsu, Hewlett-Packard (later Hewlett Packard Enterprise and HP Inc.), Intel, Lenovo, and possibly others.[67][68][69][70][71][72][73] Those researchers claimed that the bug affects systems made in 2010 or later.[74] Other reports claimed the bug also affects systems made as long ago as 2008.[75][35] The vulnerability was described as giving remote attackers:
full control of affected machines, including the ability to read and modify everything. It can be used to install persistent malware (possibly in firmware), and read and modify any data.
PLATINUM[edit]
In June 2017, the PLATINUM cybercrime group became notable for exploiting the serial over LAN (SOL) capabilities of AMT to perform data exfiltration of stolen documents.[76][77][78][79][80][81][82][83]
SA-00086[edit]
Some months after the previous bugs, and subsequent warnings from the EFF,[4] security firm Positive Technologies claimed to have developed a working exploit.[84] On 20 November, 2017 Intel confirmed that a number of serious flaws had been found in the Management Engine (mainstream), Trusted Execution Engine (tablet/mobile), and Server Platform Services (high end server) firmware, and released a 'critical firmware update'.[85][86] Essentially every Intel-based computer for the last several years, including most desktops and servers, were found to be vulnerable to having their security compromised, although all the potential routes of exploitation were not entirely known.[86] It is not possible to patch the problems from the operating system, and a firmware (UEFI, BIOS) update to the motherboard is required, which was anticipated to take quite some time for the many individual manufacturers to accomplish, if it ever would be for many systems.[39]
Affected systems[85][edit]
- Intel Atom – C3000 family
- Intel Atom – Apollo Lake E3900 series
- Intel Celeron – N and J series
- Intel Core (i3, i5, i7, i9) – 1st, 2nd, 3rd, 4th, 5th, 6th, 7th, and 8th generation
- Intel Pentium – Apollo Lake
- Intel Xeon – E3-1200 v5 and v6 product family
- Intel Xeon – Scalable family
- Intel Xeon – W family
Mitigation[edit]
None of the known unofficial methods to disable the ME prevent exploitation of the vulnerability. A firmware update by the vendor is required. However, those who discovered the vulnerability note that firmware updates are not fully effective either, as an attacker with access to the ME firmware region can simply flash an old, vulnerable version and then exploit the bug.[87]
SA-00112[edit]
In July 2018 Intel announced that 3 vulnerabilities (CVE-2018-3628, CVE-2018-3629 and CVE-2018-3632) had been discovered and that a patch for the CSME firmware would be required. Intel indicated there would be no patch for 3rd generation Core processors or earlier despite chips or their chipsets as far back as Intel Core 2 Duo vPro and Intel Centrino 2 vPro being affected.[41]
Claims that ME is a backdoor[edit]
Critics like the Electronic Frontier Foundation (EFF) and security expert Damien Zammit accused the ME of being a backdoor and a privacy concern.[88][4] Zammit stresses that the ME has full access to memory (without the parent CPU having any knowledge); has full access to the TCP/IP stack and can send and receive network packets independently of the operating system, thus bypassing its firewall.[89]
Intel responded by saying that 'Intel does not put back doors in its products nor do our products give Intel control or access to computing systems without the explicit permission of the end user.'[89] and 'Intel does not and will not design backdoors for access into its products. Recent reports claiming otherwise are misinformed and blatantly false. Intel does not participate in any efforts to decrease security of its technology.'[90]
In the context of criticism of the Intel ME and AMD Secure Technology it has been pointed out that the NSA budget request for 2013 contained a Sigint Enabling Project with the goal to 'Insert vulnerabilities into commercial encryption systems, IT systems, …' and it has been conjectured that Intel ME and AMD Secure Technology might be part of that programme.[91]
Reactions[edit]
As of 2017, Google was attempting to eliminate proprietary firmware from its servers and found that the ME was a hurdle to that.[39]
Reaction by AMD processor vendors[edit]
Shortly after SA-00086 was patched, vendors for AMD processor mainboards started shipping BIOS updates that allow disabling the AMD Secure Technology,[92] a subsystem with similar function as the ME.
Relationship between IME and Intel Active Management Technology[edit]
The Management Engine is often confused with Intel AMT. AMT runs on the ME, but is only available on processors with vPro. AMT enables owners remote administration of their computer,[89] like turning it on or off and reinstalling the operating system. However, the ME itself is built into all Intel chipsets since 2008, not only those with AMT. While AMT can be unprovisioned by the owner, there is no official, documented way to disable the ME.
See also[edit]
References[edit]
- ^ abc'Getting Started with Intel® Active Management Technology (AMT)'. Intel.
- ^ ab'Intel® AMT and the Intel® ME'. Intel.
- ^'Frequently Asked Questions for the Intel® Management Engine Verification Utility'.
Built into many Intel® Chipset–based platforms is a small, low-power computer subsystem called the Intel® Management Engine (Intel® ME).
- ^ abcPortnoy, Erica; Eckersley, Peter (May 8, 2017). 'Intel's Management Engine is a security hazard, and users need a way to disable it'.
- ^https://www.theregister.co.uk/2017/11/09/chipzilla_come_closer_closer_listen_dump_ime/
- ^https://software.intel.com/en-us/articles/getting-started-with-intel-active-management-technology-amt
- ^'Frequently Asked Questions for the Intel® Management Engine Verification Utility'.
The Intel® ME performs various tasks while the system is in sleep, during the boot process, and when your system is running.
- ^https://www.blackhat.com/eu-17/briefings/schedule/#how-to-hack-a-turned-off-computer-or-running-unsigned-code-in-intel-management-engine-8668
- ^'Frequently Asked Questions for the Intel® Management Engine Verification Utility'.
This subsystem must function correctly to get the most performance and capability from your PC.
- ^https://www.howtogeek.com/334013/intel-management-engine-explained-the-tiny-computer-inside-your-cpu/
- ^https://www.eff.org/deeplinks/2017/05/intels-management-engine-security-hazard-and-users-need-way-disable-it
- ^http://io.netgarage.org/me/
- ^https://libreboot.org/faq.html#amd
- ^'Positive Technologies Blog: Disabling Intel ME 11 via undocumented mode'. Retrieved 2017-08-30.
- ^ abIgor Skochinsky (Hex-Rays) Rootkit in your laptop, Ruxcon Breakpoint 2012
- ^'Intel Ethernet Controller I210 Datasheet'(PDF). Intel. 2013. pp. 1, 15, 52, 621–776. Retrieved 2013-11-09.
- ^'Intel Ethernet Controller X540 Product Brief'(PDF). Intel. 2012. Retrieved 2014-02-26.
- ^'Archived copy'. Archived from the original on November 1, 2014. Retrieved February 25, 2014.CS1 maint: Archived copy as title (link)
- ^ abJoanna Rutkowska. 'A Quest to the Core'(PDF). Invisiblethingslab.com. Retrieved 2016-05-25.
- ^'Archived copy'(PDF). Archived from the original(PDF) on February 11, 2014. Retrieved February 26, 2014.CS1 maint: Archived copy as title (link)
- ^'Platforms II'(PDF). Users.nik.uni-obuda.hu. Retrieved 2016-05-25.
- ^ ab'FatTwin® F618R3-FT+ F618R3-FTPT+ User's Manual'(PDF). Super Micro.
The Manageability Engine, which is an ARC controller embedded in the IOH (I/O Hub), provides Server Platform Services (SPS) to your system. The services provided by SPS are different from those provided by the ME on client platforms.
- ^'Intel® Xeon® Processor E3-1200 v6 Product Family Product Brief'. Intel.
Intel® Server Platform Services (Intel® SPS): Designed for managing rack-mount servers, Intel® Server Platform Services provides a suite of tools to control and monitor power, thermal, and resource utilization.
- ^'Intel® Xeon® Processor D-1500 Product Family'(PDF). Intel.
- ^'Intel Trusted Execution Engine Driver'. Dell.
This package provides the drivers for the Intel Trusted Execution Engine and is supported on Dell Venue 11 Pro 5130 Tablet
- ^ ab'Intel® Trusted Execution Engine Driver for Intel® NUC Kit NUC5CPYH, NUC5PPYH, NUC5PGYH'. Intel.
Installs the Intel® Trusted Execution Engine (Intel® TXE) driver and firmware for Windows® 10 and Windows 7*/8.1*, 64-bit. The Intel TXE driver is required for Secure Boot and platform security features.
- ^'Positive Technologies Blog: Disabling Intel ME 11 via undocumented mode'. Retrieved 2017-08-30.
- ^Intel ME: The Way of the Static Analysis, Troopers 2017
- ^Positive Technologies Blog:The Way of the Static Analysis
- ^ ab'Intel Hardware-based Security Technologies for Intelligent Retail Devices'(PDF). Intel.
- ^'Intel Quiet System Technology 2.0: Programmer's Reference Manual'(PDF). Intel. February 2010. Retrieved 2014-08-25.
- ^'Using Intel® AMT serial-over-LAN to the fullest'. Intel.
- ^ ab'Intel® Product Security Center'. Security-center.intel.com. Retrieved 2017-05-07.
- ^Charlie Demerjian (2017-05-01). 'Remote security exploit in all 2008+ Intel platforms'. SemiAccurate. Retrieved 2017-05-07.
- ^ abc'Red alert! Intel patches remote execution hole that's been hidden in chips since 2010'. Theregister.co.uk. Retrieved 2017-05-07.
- ^Alaoui, Youness (October 19, 2017). 'Deep dive into Intel Management Engine disablement'.
- ^Alaoui, Youness (March 9, 2017). 'Neutralizing the Intel Management Engine on Librem Laptops'.
- ^'Positive Technologies Blog: Disabling Intel ME 11 via undocumented mode'. Retrieved 2017-08-30.
- ^ abcd'Intel Patches Major Flaws in the Intel Management Engine'. Extreme Tech.
- ^https://www.theregister.co.uk/2017/12/06/intel_management_engine_pwned_by_buffer_overflow/
- ^ abhttps://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00112.html
- ^https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00125.html
- ^https://github.com/corna/me_cleaner
- ^https://www.bleepingcomputer.com/news/hardware/researchers-find-a-way-to-disable-much-hated-intel-me-component-courtesy-of-the-nsa/
- ^https://www.theregister.co.uk/2017/08/29/intel_management_engine_can_be_disabled/
- ^http://blog.ptsecurity.com/2017/08/disabling-intel-me.html
- ^http://blog.ptsecurity.com/2017/08/disabling-intel-me.html
- ^https://github.com/corna/me_cleaner/wiki/HAP-AltMeDisable-bit
- ^https://github.com/corna/me_cleaner/commit/ced3b46ba2ccd74602b892f9594763ef34671652
- ^https://web.archive.org/web/20160616070449/https://puri.sm/posts/petition-for-intel-to-release-an-me-less-cpu-design/
- ^Alaoui, Youness (2017-03-09). 'Neutralizing the Intel Management Engine on Librem Laptops'. puri.sm. Retrieved 2017-12-13.
- ^https://puri.sm/posts/purism-librem-laptops-completely-disable-intel-management-engine/
- ^http://blog.system76.com/post/168050597573/system76-me-firmware-updates-plan
- ^https://liliputing.com/2017/12/dell-also-sells-laptops-intel-management-engine-disabled.html
- ^https://www.extremetech.com/computing/260219-dell-sells-pcs-without-intel-management-engine-tradeoffs
- ^https://www.heise.de/newsticker/meldung/Dell-schaltet-Intel-Management-Engine-in-Spezial-Notebooks-ab-3909860.html
- ^http://www.dell.com/support/manuals/us/en/04/latitude-14-5414-laptop/5414_om/stealth-mode?guid=guid-3655713b-6a1b-46a8-ba69-eaa3c324b3cd&lang=en-us
- ^https://www.theregister.co.uk/2017/12/06/intel_management_engine_pwned_by_buffer_overflow/
- ^https://twitter.com/rootkovska/status/938458875522666497
- ^'Invisible Things Lab to present two new technical presentations disclosing system-level vulnerabilities affecting modern PC hardware at its core'(PDF). Invisiblethingslab.com. Retrieved 2016-05-25.
- ^'Berlin Institute of Technology : FG Security in telecommunications : Evaluating 'Ring-3' Rootkits'(PDF). Stewin.org. Retrieved 2016-05-25.
- ^'Persistent, Stealthy Remote-controlled Dedicated Hardware Malware'(PDF). Stewin.org. Retrieved 2016-05-25.
- ^'Security Evaluation of Intel's Active Management Technology'(PDF). Web.it.kth.se. Retrieved 2016-05-25.
- ^'CVE - CVE-2017-5689'. Cve.mitre.org. Retrieved 2017-05-07.
- ^'Intel Hidden Management Engine - x86 Security Risk?'. Darknet. 2016-06-16. Retrieved 2017-05-07.
- ^Garrett, Matthew (2017-05-01). 'Intel's remote AMT vulnerablity'. mjg59.dreamwidth.org. Retrieved 2017-05-07.
- ^ abc'2017-05-05 ALERT! Intel AMT EXPLOIT OUT! IT'S BAD! DISABLE AMT NOW!'. Ssh.comAccessdate=2017-05-07.
- ^Dan Goodin (2017-05-06). 'The hijacking flaw that lurked in Intel chips is worse than anyone thought'. Ars Technica. Retrieved 2017-05-08.
- ^'General: BIOS updates due to Intel AMT IME vulnerability - General Hardware - Laptop - Dell Community'. En.community.dell.com. Retrieved 2017-05-07.
- ^'Advisory note: Intel Firmware vulnerability – Fujitsu Technical Support pages from Fujitsu Fujitsu Continental Europe, Middle East, Africa & India'. Support.ts.fujitsu.com. 2017-05-01. Retrieved 2017-05-08.
- ^'HPE HPE CS700 2.0 for VMware'. H22208.www2.hpe.com. 2017-05-01. Retrieved 2017-05-07.
- ^'Intel® Security Advisory regarding escalation o. Intel Communities'. Communities.intel.com. Retrieved 2017-05-07.
- ^'Intel Active Management Technology, Intel Small Business Technology, and Intel Standard Manageability Remote Privilege Escalation'. Support.lenovo.com. Retrieved 2017-05-07.
- ^'MythBusters: CVE-2017-5689'. Embedi.com. Retrieved 2017-05-07.
- ^Charlie Demerjian (2017-05-01). 'Remote security exploit in all 2008+ Intel platforms'. SemiAccurate.com. Retrieved 2017-05-07.
- ^'Sneaky hackers use Intel management tools to bypass Windows firewall'. Retrieved 10 June 2017.
- ^Tung, Liam. 'Windows firewall dodged by 'hot-patching' spies using Intel AMT, says Microsoft - ZDNet'. Retrieved 10 June 2017.
- ^'PLATINUM continues to evolve, find ways to maintain invisibility'. Retrieved 10 June 2017.
- ^'Malware Uses Obscure Intel CPU Feature to Steal Data and Avoid Firewalls'. Retrieved 10 June 2017.
- ^'Hackers abuse low-level management feature for invisible backdoor'. iTnews. Retrieved 10 June 2017.
- ^'Vxers exploit Intel's Active Management for malware-over-LAN • The Register'. www.theregister.co.uk. Retrieved 10 June 2017.
- ^Security, heise. 'Intel-Fernwartung AMT bei Angriffen auf PCs genutzt'. Security. Retrieved 10 June 2017.
- ^'PLATINUM activity group file-transfer method using Intel AMT SOL'. Channel 9. Retrieved 10 June 2017.
- ^How to Hack a Turned-Off Computer, or Running Unsigned Code in Intel Management Engine Black Hat Europe 2017
- ^ ab'Intel® Management Engine Critical Firmware Update (Intel SA-00086)'. Intel.
- ^ ab'Intel Chip Flaws Leave Millions of Devices Exposed'. Wired.
- ^https://www.theregister.co.uk/2017/12/06/intel_management_engine_pwned_by_buffer_overflow/
- ^'Intel x86 CPUs Come with a Secret Backdoor That Nobody Can Touch or Disable'.
- ^ abcWallen, Jack (July 1, 2016). 'Is the Intel Management Engine a backdoor?'.
- ^https://www.theregister.co.uk/2017/08/29/intel_management_engine_can_be_disabled/
- ^https://www.heise.de/ct/ausgabe/2018-7-Briefe-E-Mail-Hotline-3992838.html#p_41
- ^'AMD Reportedly Allows Disabling PSP Secure Processor With Latest AGESA - Phoronix'. www.phoronix.com. 7 December 2017. Retrieved 2019-04-16.
External links[edit]
- Slides by Igor Skochinsky: